
Innovation at
The Frontier
From Artificial Intelligence to Cybersecurity, explore the groundbreaking research conducted by CSI faculty and students.

Pushing the Boundaries of
Computer Science
Our faculty are leaders in their fields, driving innovation in AI, Cybersecurity, Imaging, and Data Science right here at CSI.
Faculty Directory
Meet the minds shaping the future of technology.

Prof. Sos Agaian
Big and Small Data Analytics, Multimodal Biometric and Digital Forensics, Information Processing and Fusion.

Prof. Feng Gu
Complex Systems, High Performance Computing, and Bioinformatics research focusing on large-scale simulations.

Prof. Yumei Huo
Design and Analysis of Algorithms, Sequence Scheduling, Combinatorial Optimization, and Operations Research.

Prof. Anatoliy Gordonov
Graph Theory and Network Structure Optimization, Real Time Control Systems, and Formal Languages.

Prof. Louis Petingi
Extremal Graph Theory and its applications to the reliability and performance of communication networks.

Prof. Natacha Gueorguieva
Pattern Recognition, Clustering, and Brain Modeling. Simulations of Spiking Neurons and Self-Organizing Maps.

Prof. Susan Imberman
Focus on educational data mining and the application of machine learning to robotics control systems.

Prof. Deborah Sturm
Image Processing, Visualization, and Root Cause Analysis of Errors. Also focuses on Game Development education.
Prof. Sarah Zelikovitz
Semi-Supervised Machine Learning, Text Classification/Categorization, and Information Retrieval systems.

Prof. Shuqun Zhang
Image and Video Processing, Computer Vision, Pattern Recognition, and Digital Holography.

Prof. Xiaowen Zhang
Information Security, Quantum Computing, Wireless Communications, and Network Security protocols.

Prof. Zhanyang Zhang
Database Theory, Business Intelligence, RFID applications, and Underwater Wireless Sensor Networks.
Student Innovation
From cybersecurity algorithms to social computing, our undergraduate and graduate students are publishing work that solves real-world problems.

Optimized Tunel Image Enhancement
Advanced algorithms for clarifying low-light tunnel imagery for safety systems.
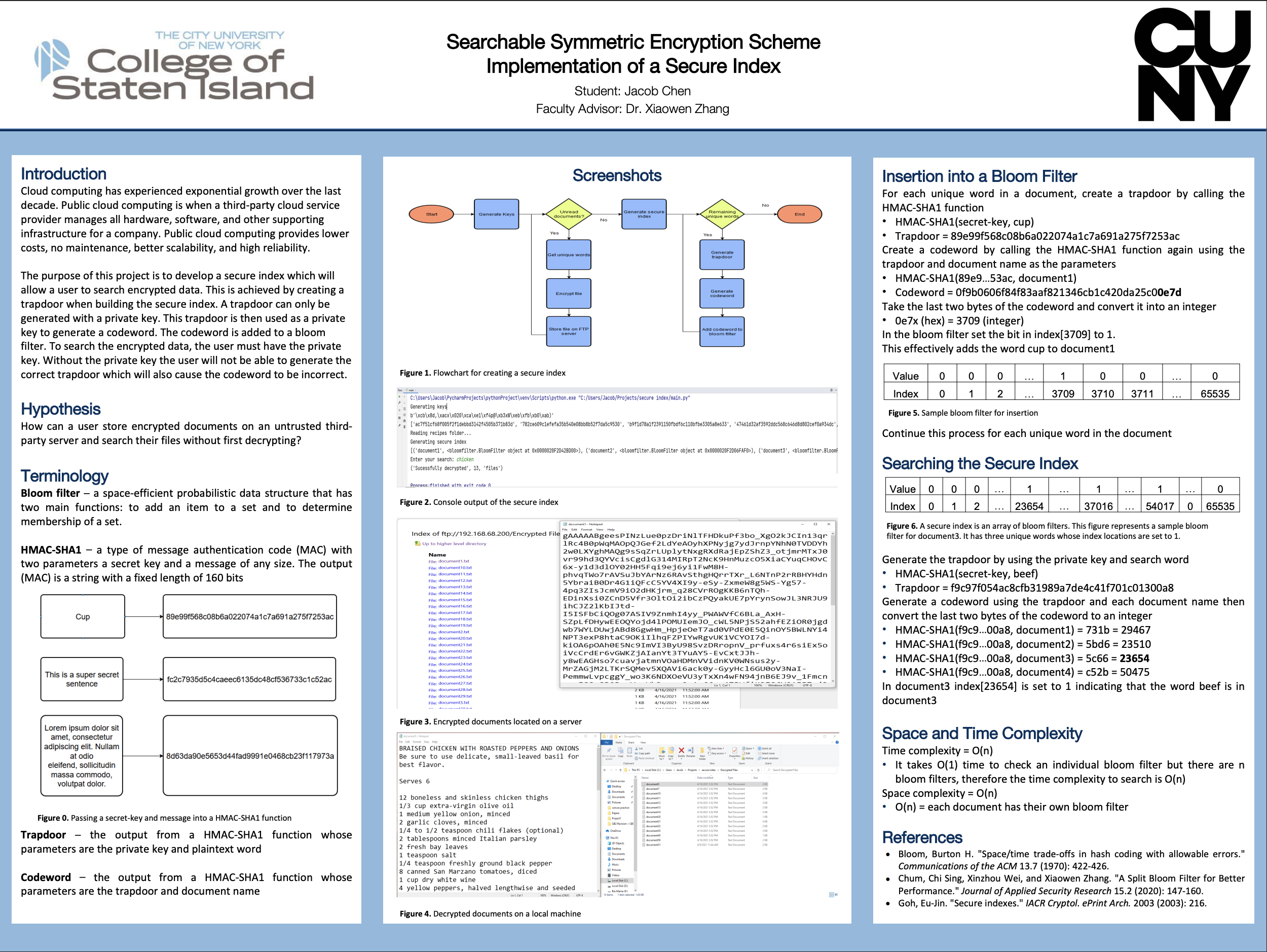
Searchable Symmetric Encryption Scheme
Implementation of a secure index for encrypted database querying.

Haunted Decoder: Binary Conversion Game
Gamifying computer science fundamentals for ed-tech.
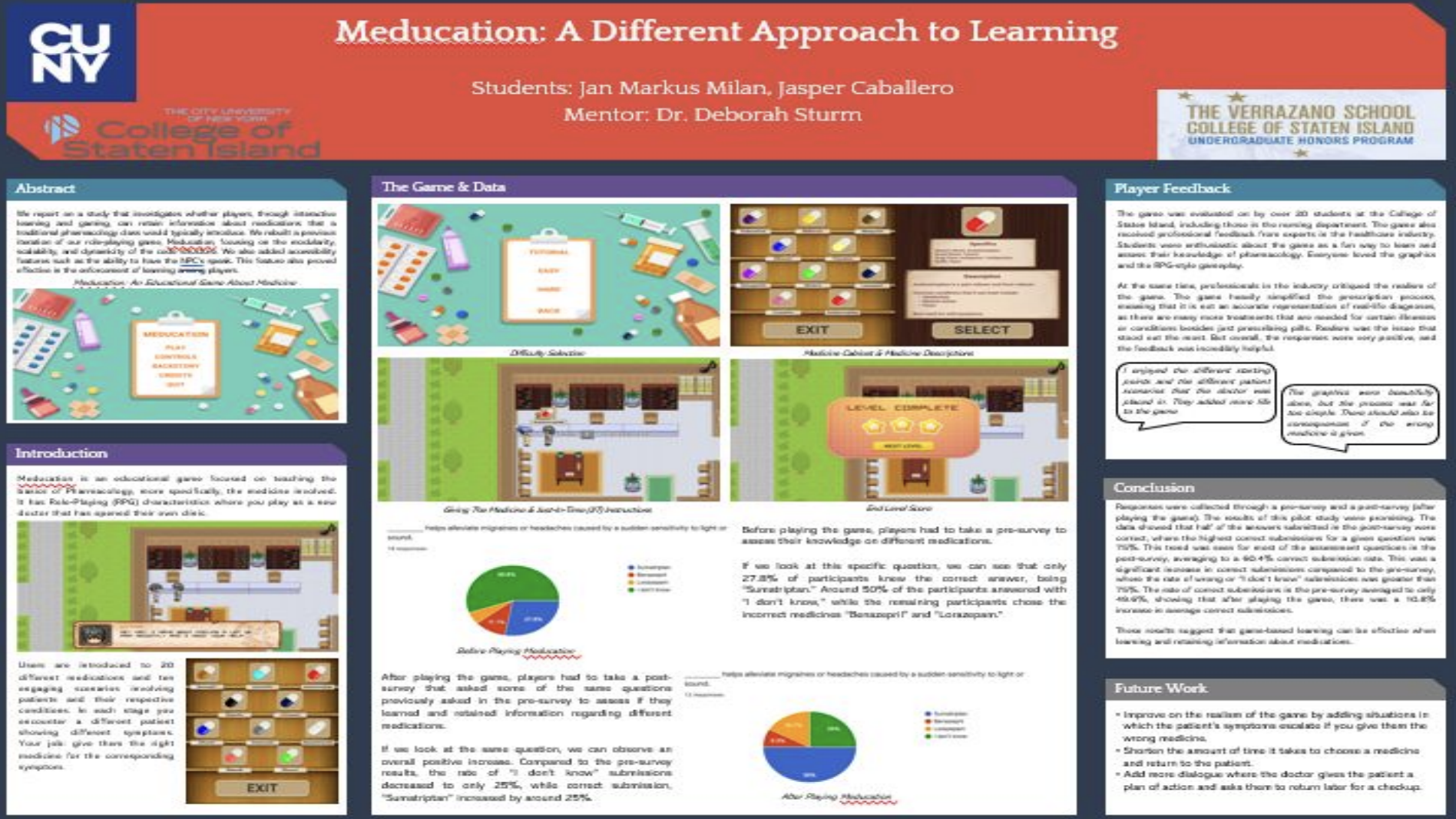
Meducation: A Different Approach to Learning
Interactive medical education platform for students.
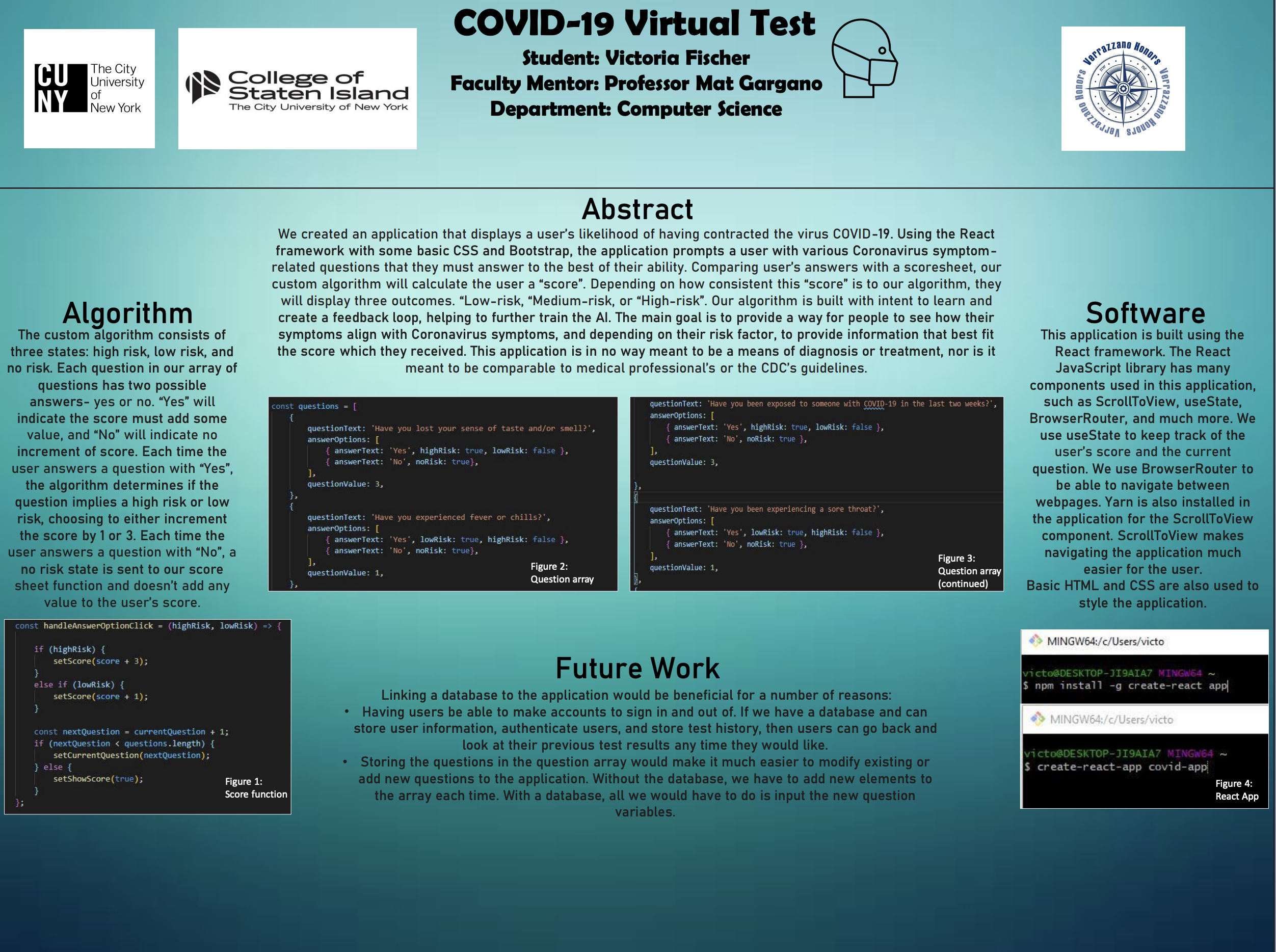
COVID-19 Virtual Test
Simulation software for pandemic response tracking.
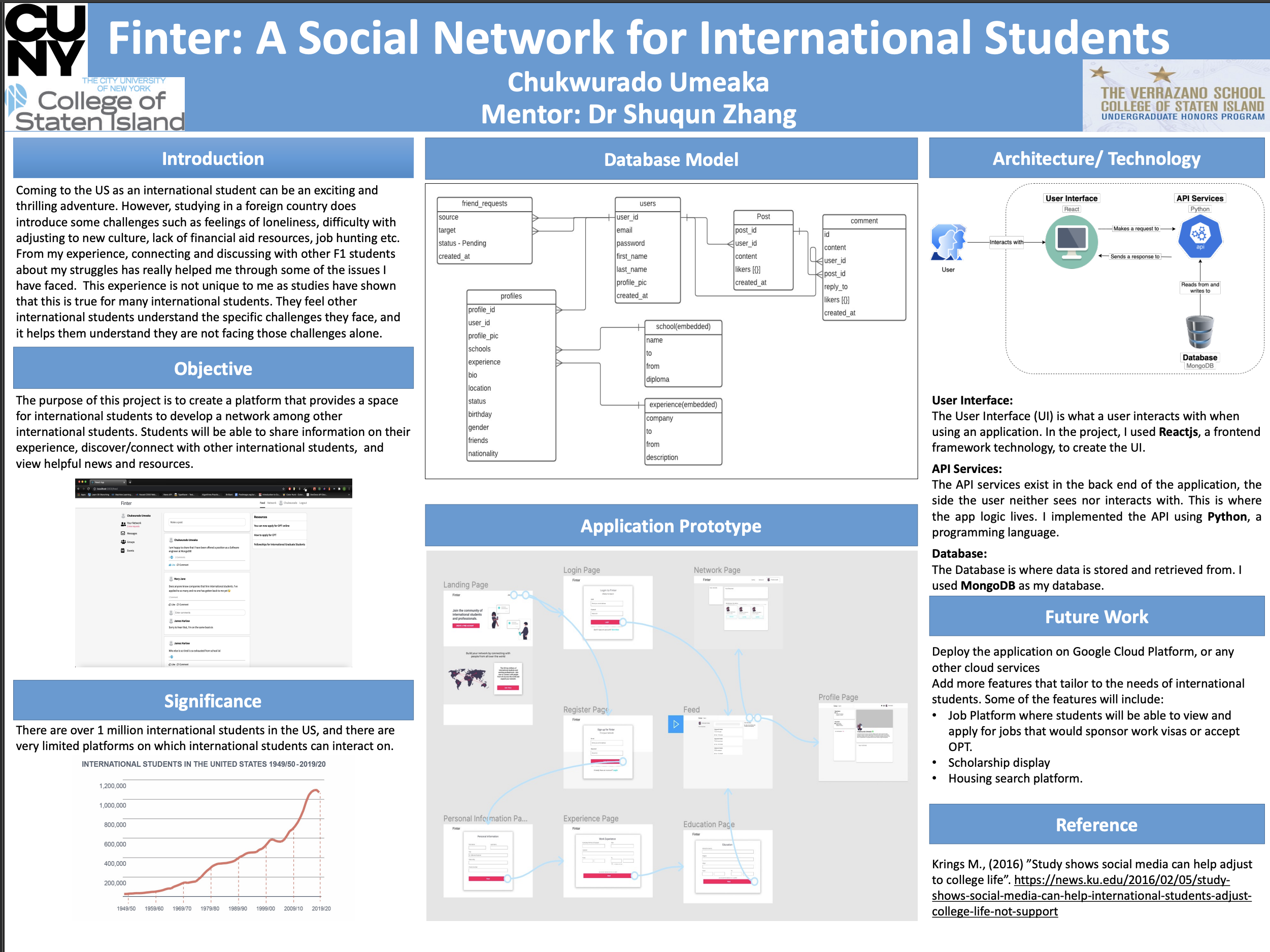
Finter: Social Network for Int'l Students
Connecting students across borders to ease cultural transition.

User Density & Spatial Cloaking Algorithms
Improving privacy protection for mobile users in location-based services.
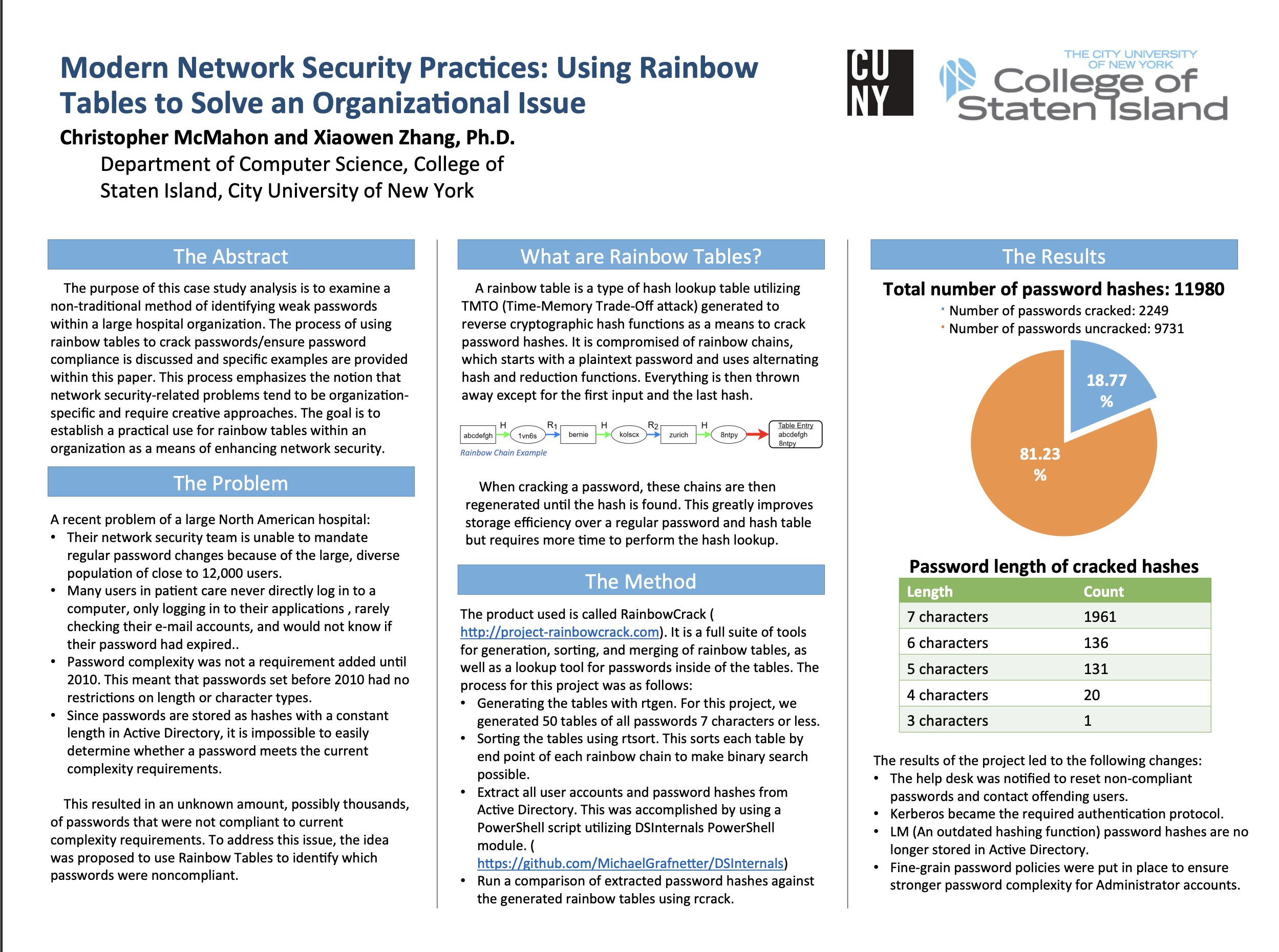
Modern Network Security Practices
Using Rainbow Tables to solve organizational password security issues.

QR Code Assisted OTP Authentication
A mutual authentication scheme for secure logins.
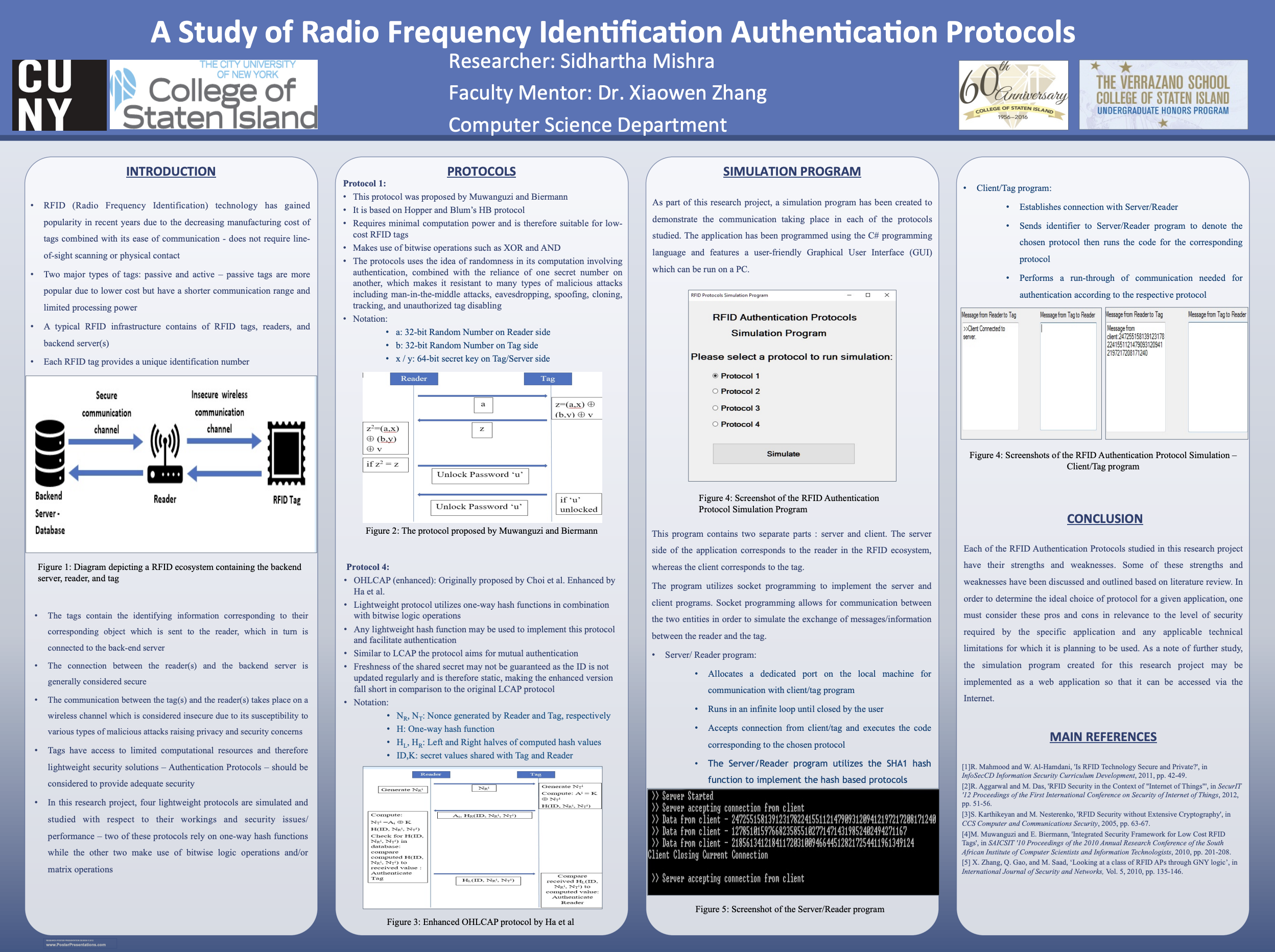
RFID Authentication Protocols Study
Analysis of radio frequency identification security vulnerabilities.

Secure Deletion File System
Designing storage systems that ensure permanent data erasure.

Bypassing Wireless Authentication
Vulnerability assessment of web-based wireless gateway systems.
Interested in getting involved?